News
Study Shows Confusion over Cloud Security Responsibilities
Despite the well-known benefits of cloud computing, it entails new security risks, such as databases hijacked for ransom and unencrypted data stores. While such vulnerabilities are continually trumpeted in the headlines, there still persists general confusion in the space about who exactly is responsible for security: cloud vendors or users.
That's a key takeaway from a recent report from Barracuda Networks Inc. titled "Steps to Secure Your Journey to the Public Cloud: Challenges, Misconceptions and Opportunities of Shared Responsibility," based on a survey of 550 IT decision makers in the Europe, Middle East and Africa (EMEA) region.
"The root cause of many public cloud concerns is a lack of clarity over the shared responsibility model," Barracuda said in a blog post last week. "Many IT buyers assume that because they're effectively outsourcing the running of their infrastructure to a trusted third party, the provider will take care of everything. This simply isn't the case."
This confusion over the shared responsibility model -- in which the provider spells out who is responsible for what -- and perhaps-related security risks actually could be hindering cloud adoption, Barracuda claimed, or even opening up organizations to new attack vectors.
What's more, the confusion persists despite explicit guidance from major cloud providers such as Amazon Web Services Inc. (AWS) and Microsoft Azure.
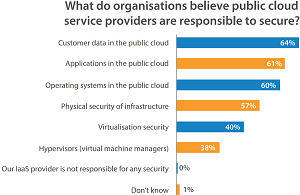 [Click on image for larger view.]
Where Does the Security Responsibility Lie? (source: Barracuda Networks)
[Click on image for larger view.]
Where Does the Security Responsibility Lie? (source: Barracuda Networks)
The AWS site for the Shared Responsibility Model, for example, clearly states: "While AWS manages security of the cloud, security in the cloud is the responsibility of the customer. Customers retain control of what security they choose to implement to protect their own content, platform, applications, systems and networks, no differently than they would for applications in an on-site datacenter."
Microsoft offers its own Azure guidance in "What Does Shared Responsibility in the Cloud Mean?" which says security responsibilities depend on the model of cloud computing being used: Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS) or Software-as-a-Service (SaaS).
"Who is responsible for what (in terms of security) depends on the cloud service model you use (IaaS/PaaS/SaaS)," Microsoft says. "With IaaS, the cloud service provider is responsible for the core infrastructure security, which includes storage, networking and compute (at least at the fabric level -- the physical level).
"As you move from IaaS, to PaaS and then to SaaS, you'll find that you're responsible for less and the cloud service provider is responsible for more."
Whatever model is used, Microsoft says, the responsibility for "data classification and accountability" is always the domain of the cloud customer. Also, Microsoft customers are almost always responsible for "client and end-point protection," except for the SaaS model, where that responsibility is split between user and provider.
"This is problematic when one considers the answers to the Barracuda Networks survey, in which the vast majority of IT leaders claimed that their public IaaS provider is responsible for securing customer data in the public cloud (64 percent), securing applications (61 percent) and operating systems (60 percent)," Barracuda said. "This is completely at odds with what AWS, Microsoft, and others say, exposing countless organizations to unnecessary risk. The fact that 61 percent across EMEA claim to fully understand their cloud obligations further underlines the dangerous disconnect between perception and reality when it comes to public cloud security."
Besides security responsibility, other data points from the report include:
- Respondents claimed nearly 35 percent of their infrastructure is currently in the public cloud, and predicted this will rise to half in two years' time and then to more than three-fifths (62 percent) in five years.
- 20 percent of responding organizations' annual IT budgets currently being spent on cloud deployments.
- 60 percent of firms reported having already been hit by a cyberattack and an additional 26 percent are expecting one in the future.
- Less than half (45 percent) of respondents believe that their public cloud IaaS provider completely offers strong protection when it comes to accessing cloud applications.
- The most popular use case for cloud computing is data storage (77 percent), followed by data recovery (56 percent), Web and app hosting (54 percent), data analytics (51 percent) and CRM systems (46 percent).
- Sensitive data being stored in the cloud includes: employee information (48 percent), business IP (42 percent) and customer bank details (40 percent).
- Top threats include: phishing (49 percent), DDoS (44 percent), ransomware (40 percent) and advanced persistent threats (APTs) (39 percent).
Barracuda noted that more than half of respondents said they are implementing additional security measures in their cloud environments. Some of the recommended options to do this include:
- Web Application Firewalls (WAFs)
- Strong data encryption
- Identity and access controls
- Next Generation Firewalls (NGFWs)
- Message archiving
- IDS/IPS
- DDoS mitigation
- Logging and monitoring
- SIEM
- Endpoint protection
- Data protection and archiving
"The bottom line is that organizations are continuing to invest in public cloud projects, but they need a trusted vendor-neutral partner to help them navigate the choppy waters of cybersecurity if they want to minimize risk in the process," said Barracuda, which added that it has already addressed many of the challenges mentioned in the survey and is a "great choice" for organizations moving to the cloud.
About the Author
David Ramel is an editor and writer at Converge 360.