AWS Step-by-Step
Extending Active Directory to the AWS Cloud
Making on-premises Active Directory available to resources in the AWS cloud involves using the AD Connector option and a gateway VPN connection.
In my last column, I explained that Amazon Web Services (AWS) provides cloud-based directory services that are based on Microsoft Active Directory.
That column focused on creating a brand-new, cloud-based Active Directory environment. However, it is also possible to make your on-premises Active Directory accessible to AWS. In this post, I will show you how.
You will need to begin the process by signing in to the AWS Console. Upon doing so, go to the console's Home screen, and then click on the Directory Service link, located in the Security & Identity section. This will cause the console to take you to the AWS Directory Service screen, shown in Figure 1.
 [Click on image for larger view.] Figure 1: Click the Get Started Now button.
[Click on image for larger view.] Figure 1: Click the Get Started Now button.
As you can see, this is an informational screen. You can use this screen to get information on creating a directory, connecting to the cloud or managing access, but you can't actually create or extend an Active Directory from this screen. That being the case, click on the Get Started Now button, shown in Figure 1.
At this point, you will be taken to the Choose Directory Type screen, shown in Figure 2. As you can see, AWS provides three Active Directory options. The first of these options is the Microsoft AD. This is the option that you would use if you wanted to create an entirely cloud-based Active Directory. If you are interested in using this option, then please be sure to check out my column on the subject.
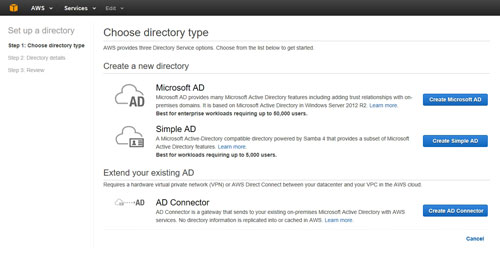 [Click on image for larger view.] Figure 2: The Choose Directory Type screen allows you to choose the type of Active Directory that you want to create.
[Click on image for larger view.] Figure 2: The Choose Directory Type screen allows you to choose the type of Active Directory that you want to create.
The second option is to create a simple Active Directory. A simple Active Directory is kind of like an Active Directory emulator. It isn't really a Microsoft Active Directory at all. In fact, the directory is based on Samba. Even so, the Simple AD is Active Directory-compatible and provides most of the more important Active Directory features and capabilities. I tend to think of the Simple AD as being similar to LDAP in that it is a lightweight directory environment.
The third option is the AD Connector. The AD Connector is what you would choose if you wanted to link your on-premises Active Directory environment to the AWS cloud.
The first thing that you must understand about the AD Connector is that it is not merely a cloud-based domain controller. In other words, you are not synchronizing your on-premises Active Directory to a cloud-based domain controller. Doing so would require the cloud-based domain controller to be domain-joined, and there would have to be a mechanism for securely synchronizing directory information.
Instead, the AD Connector is a proxy service. As such, it does not require Active Directory synchronization. The AD Connector works by forwarding requests (such as sign-in requests or query requests) to your on-premises domain controllers. Because the AD Connector is not actually synchronizing your domain controllers to the cloud, you will not have to change the way that you perform Active Directory management. You can still, for instance, use the Active Directory Users and Computers console to create, edit and delete user accounts.
If you click on the Create AD Connector button, you will be taken to a screen that asks you to provide some basic information about your on-premises Active Directory. For example, you will be asked for the DNS server name, a user name and password, and the DNS server's IP address. You can see what these options look like in Figure 3.
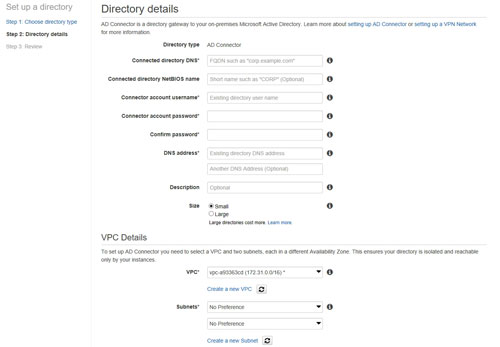 [Click on image for larger view.] Figure 3: The console asks for some basic information about your environment.
[Click on image for larger view.] Figure 3: The console asks for some basic information about your environment.
As you can see, the information that AWS asks for is pretty basic. I am guessing that the process of entering the required information is going to be largely self-explanatory. If you need some extra help, however, you can check out the AWS documentation or read my previous column.
In order for the AD Connector to work, you are going to need a way for AWS to communicate with your network. Remember that just because you are able to communicate with AWS through the console, that does not mean that AWS is able to see into your network. That being the case, you are going to need to create a virtual private gateway The virtual private gateway is one half of the VPN connection between your organization and AWS. The virtual private gateway resides on AWS.
The other half of the VPN is a VPN connection into your on-premises network. AWS refers to this as a customer gateway. AWS expects you to connect the virtual private gateway to the customer gateway in an effort to establish communications between your network and AWS.
In summary, making your Active Directory available to resources in the AWS cloud involves using AD Connector and a gateway VPN connection. You can find the documentation for the VPN connection here. I will also be discussing the VPN configuration process in an upcoming article.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.