AWS Step-by-Step
Connecting to an EC2 Instance Using EC2 Instance Connect, Part 1
One of the more welcome changes that Amazon has made to its AWS cloud is the introduction of a feature called EC2 Instance Connect. EC2 Instance Connect Endpoint makes it easier to connect to a Linux virtual machine instance running on EC2. Depending on the use case, EC2 Instance Connect can potentially even improve your overall security while lowering your costs at the same time. In this article series, I want to delve into EC2 Instance Connect. As I do, I will show you how to use it and I will explain why this feature is so helpful.
At its simplest, EC2 Instance Connect is a tool for connecting to a Linux instance through your browser. Previously, connecting to a Linux instance meant using SSH or perhaps PUTTY. Now however, you can simply connect to the instance through your browser. Better still, the process of establishing connectivity is completely point and click. There is no need for looking up the instance's IP address or for supplying a private key file.
To show you just how easy it is to connect to an instance through EC2 Instance Connect, take a look at Figure 1. I have created a Linux instance and then selected the instance within the EC2 console and clicked Connect. This took me to the screen shown in the figure. To connect I need only to choose the Connect Using EC2 Instance Connect option, select the instance's IP address, and click Connect. The instance's console is made available through the browser, as shown in Figure 2.
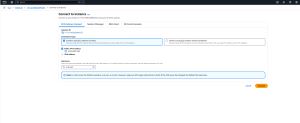 [Click on image for larger view.] Figure 1: This Is What the EC2 Instance Connect Screen Looks Like.
[Click on image for larger view.] Figure 1: This Is What the EC2 Instance Connect Screen Looks Like.
 [Click on image for larger view.] Figure 2: I Was Able To Effortlessly Connect To My Instance Through The Browser.
[Click on image for larger view.] Figure 2: I Was Able To Effortlessly Connect To My Instance Through The Browser.
There are of course, some prerequisites that you will need to meet in order to use EC2 Instance Connect. If you are creating new instances however, you may find that these prerequisites are met by default.
The first prerequisite is that you will need to make sure that the EC2 Instance Connect software is installed within your EC2 instance. Most of the current Linux AMIs provided by Amazon already have EC2 Instance Connect preinstalled. These AMIs include:
- AL2023 standard AMI
- Amazon Linux 2 2.0.20190618 or later
- macOS Sonoma 14.2.1 or later
- macOS Ventura 13.6.3 or later
- macOS Monterey 12.7.2 or later
- Ubuntu 20.04 or later
If you happen to be using an instance that is based on an AMI other than the ones that are listed here, you may still be able to take advantage of EC2 Instance Connect. Amazon provides instructions for manually installing the software onto other supported Linux instances.
The second requirement in order to use EC2 Instance Connect is that you will need to have IP connectivity to the instance. Ideally, this means that your instance should be provisioned with a public IPv4 or IPv6 address and that the instance should reside in a subnet that provides a route to the Internet (including any necessary routing table entries).
Even though using a public IP address is the easiest way to make the instance accessible through EC2 Instance Connect, it's not the only option. As an alternative, you can use connect using your instance's private IPv4 address, so long as some sort of route exists that will allow external access to the instance. For example, you might configure AWS Direct Connect or you could set up a site to site VPN.
If neither of these options work, there is a third connectivity option that I plan to talk about in Part 2 of this series.
The third requirement is that the security group that is associated with the instance must be configured to allow inbound SSH traffic. If you would prefer not to create a blanket rule that allows SSH traffic from any source, which would constitute a security risk, then you will need to design the rule so that it allows SSH traffic that is coming from the EC2 Instance Connect Service. The prefixes used by the EC2 Instance Connect Service are:
- com.amazonaws.region.ec2-instance-connect
- com.amazonaws.region.ipv6.ec2-instance-connect
The first of these prefixes is for IPv4 traffic, while the second is for IPv6 traffic. In both cases, you will need to substitute the region name for the word region.
The last prerequisite that you will have to meet involves making sure that you have the appropriate permissions in place. Again, if you are creating a brand-new instance, there is a chance that you won't have to worry about this one.
If you look back at Figure 1, you will notice that there is a Username field. This field is automatically populated with the text EC2-user. This username is hard coded into the AMI, thereby ensuring that this user has the necessary access. You can however, grant access to a different user account by following the steps that Amazon provides here.
Now that I have shown you how to make EC2 Instance Connect work, I want to follow up on this discussion in Part 2 by talking about an optional component called EC2 Instance Connect endpoint.
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.