News
AWS Fights Off New Type of DDoS Attack
Amazon Web Services (AWS) detailed how its cloud computing infrastructure successfully thwarted a wave of distributed denial-of-service (DDoS) attacks that used a new technique to try to overwhelm servers and networks with internet traffic.
The cloud giant yesterday (Oct. 10) joined fellow industry players such as Google and Cloudflare in publicizing a recent onslaught of DDoS attacks that are not only increasing in frequency, but also size.
In fact, Google said it fought off the largest DDoS attack ever recorded, peaking at 398 million requests per second (rps).
The wave of attacks appears to have picked up steam in August and really hit stride in September, using a technique dubbed the "HTTP/2 rapid reset attack."
AWS yesterday posted this security bulletin about CVE-2023-44487, entered into the National Vulnerability Database to track fixes to various HTTP/2 implementations:
Publication Date: 2023/10/10 05:00 AM PDT
AWS is aware of CVE-2023-44487, also known as "HTTP/2 Rapid Reset Attack," related to HTTP/2 capable web servers where rapid stream generation and cancellation can result in additional load which could lead to a Denial of Service. AWS infrastructure is designed with various protections to address Layer 7 request floods, however, we have implemented additional mitigations to address this issue. AWS also recommends customers who operate their own HTTP/2 capable web servers verify with their web server vendor to determine if they are affected and, if so, install the latest patches from their respective vendors to address this issue.
Customers can learn more about this in the AWS Security blog post, titled "How AWS Protects Customers from DDoS Events".
The referenced blog post explains more.
"Between August 28 and August 29, 2023, proactive monitoring by AWS detected an unusual spike in HTTP/2 requests to Amazon CloudFront, peaking at over 155 million requests per second (RPS)," AWS said. "Within minutes, AWS determined the nature of this unusual activity and found that CloudFront had automatically mitigated a new type of HTTP request flood DDoS event, now called an HTTP/2 rapid reset attack. Over those two days, AWS observed and mitigated over a dozen HTTP/2 rapid reset events, and through the month of September, continued to see this new type of HTTP/2 request flood."
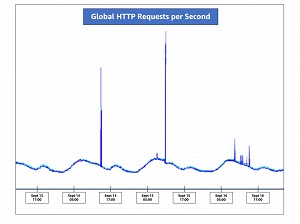 [Click on image for larger view.] Global HTTP requests per second, September 13 - 16 (source: AWS).
[Click on image for larger view.] Global HTTP requests per second, September 13 - 16 (source: AWS).
The graphic above shows how requests per second spiked in mid September.
To defend against these sorts of DDoS attacks, AWS said organizations can implement an architecture to help them specifically detect unwanted requests as well as scale to absorb and block malicious HTTP requests, offering up its own services as examples. It codified its guidance in the AWS Best Practices for DDoS Resiliency document, updated Aug. 9.
About the Author
David Ramel is an editor and writer at Converge 360.