News
AWS Buckles Down on S3 Security with Encryption, Access Improvements
A critical spotlight has been trained on the Amazon S3 storage service in recent months over a rash of high-profile data exposures caused by misconfigured security and accessibility settings.
Perhaps in an effort to course-correct, Amazon Web Services (AWS) this week announced a handful of new features aimed at beefing up S3 security.
First, the S3 console now makes it easier for administrators to identify which storage buckets are configured for public access. The new Bucket Permissions Check feature also identifies the avenue of the public access, whether it's through a change in the bucket access control list (ACL) or in the bucket policy itself. The feature is designed to let users "see the impact of changes to [their] bucket policies and ACLs as soon as [they] make them," said AWS evangelist Jeff Barr in a blog post Monday.
The new public-access alerts on the S3 console look like this:
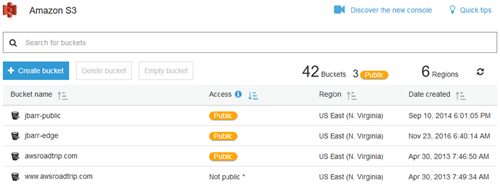 [Click on image for larger view.] The Bucket Permissions Check feature in the Amazon S3 console makes it easy to identify which buckets allow public access. (Source: AWS/Jeff Barr)
[Click on image for larger view.] The Bucket Permissions Check feature in the Amazon S3 console makes it easy to identify which buckets allow public access. (Source: AWS/Jeff Barr)
Second, a new "default encryption" setting prompts S3 to automatically apply server-side encryption to new objects that don't already have it. Administrators can choose ahead of time which type of encryption they want S3 to automatically apply -- S3 managed keys or AWS Key Management Service (KMS) keys.
"If an unencrypted object is presented to S3 and the configuration indicates that encryption must be used, the object will be encrypted using encryption option specified for the bucket," Barr said.
Third, the S3 Inventory tool now lets administrators choose to receive regular reports on the encryption levels of the objects in their buckets. This new capability in the S3 Inventory tool is also useful for organizations performing compliance auditing, AWS noted.
The last two feature updates are related to the Cross-Region Replication (CRR) capability in S3, which lets users replicate objects to and from buckets located in different AWS regions.
AWS on Monday announced that CRR can now replicate objects protected by KMS keys. Previously, this had been a problem because KMS keys are region-specific. Now, Barr explained, administrators can "choose the destination key when [they] set up cross-region replication. During the replication process, encrypted objects are replicated to the destination over an SSL connection. At the destination, the data key is encrypted with the KMS master key [the administrator] specified in the replication configuration. The object remains in its original, encrypted form throughout; only the envelope containing the keys is actually changed."
Finally, the CRR can now change the ownership of a replicated object when it lands in the destination bucket, as well as revoke ownership of the replicated object from the previous bucket owner. "With this change, ownership of the source and the destination data is split across AWS accounts, allowing you to maintain separate and distinct stacks of ownership for the original objects and their replicas," Barr said.
Each of the new S3 features come at no additional cost and are immediately available in every AWS region except for Beijing.