News
Researchers Launch Open Source Tool To Protect Amazon S3 Buckets
The Kromtech Security Center has released a free open source tool to help organizations detect unsecured Amazon Simple Storage Service (S3) buckets in their environments.
Reports of unsecured Amazon S3 buckets exposing sensitive data to the public Internet have become alarmingly commonplace in recent months. Since this summer, the Republican National Committee, Verizon, Dow Jones & Company, the Chicago Election Board, military contractor TigerSwan, Viacom and IT services giant Accenture have all been discovered to have misconfigured their Amazon S3 buckets to allow public access, exposing the personal data of hundreds of millions of individuals, as well as critical information related to their own IT infrastructures.
The problem has become so prevalent that it prompted Amazon Web Services (AWS) to issue a pointed reminder to its users to ensure that their Amazon S3 buckets are properly configured. Amazon S3 misconfigurations are almost entirely the result of human error; access to Amazon S3 buckets are set to private by default.
Nevertheless, there are indications that Amazon S3 security misconfigurations are on the rise, and often go undetected by the organizations who use the service to store and manage their data in the cloud.
In an effort to stem the wave of Amazon S3-related data exposures, researchers at Kromtech have developed the Kromtech S3 Inspector. Available at GitHub here, the Kromtech S3 Inspector scans organizations' AWS environments for any Amazon S3 buckets that are configured for public access.
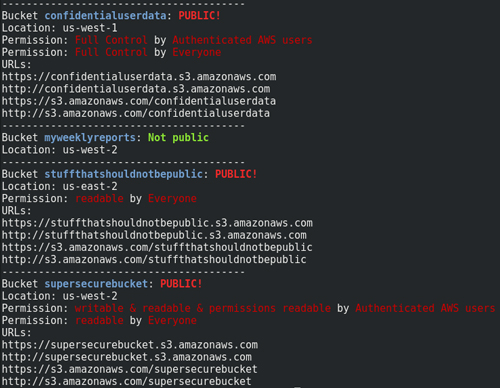 [Click on image for larger view.] The Kromtech S3 Inspector scans an organization's AWS environment and alerts users when it finds an unsecured Amazon S3 bucket. (Source: Kromtech)
[Click on image for larger view.] The Kromtech S3 Inspector scans an organization's AWS environment and alerts users when it finds an unsecured Amazon S3 bucket. (Source: Kromtech)
"The tool gives users a report that they can then use to shut down any unwanted public access to the S3 buckets and the valuable data they contain," said Kromtech researchers in a blog post last week announcing the tool's release.
The company plans to add more scanning and security features to the tool in future updates.
The researchers said they developed the tool after spending the last few years discovering "thousands of S3 services left open for public access." Kromtech has reported each instance it has discovered and even published an in-depth guide for organizations explaining how to secure Amazon S3 buckets.
"However, despite numerous warnings and a never ending cycle of data leaks, it seemed like those who store sensitive data online were not getting the message or unaware of the dangers," the researchers said.
Kromtech said it hopes the combination of an easy-to-use tool, on top of its ongoing effort to raise public awareness of Amazon S3 data exposures, will encourage more organizations to take stock of their AWS environments for potential security weaknesses.