AWS Step-by-Step
What You Need To Know About VPC Security Groups
Here's a quick rundown of what a VPC security group is, what it does, and some of the rules you'll need to keep in mind when creating and working with them in AWS.
I recently wrote a column in which I explained the process for creating a virtual private cloud (VPC) in Amazon Web Services (AWS). In that article, I briefly mentioned the concept of VPC security groups, but I didn't really get a chance to explore the topic.
Therefore, I want to use this column to explain what a VPC security group is, what it does, and some of the key considerations that you will need to keep in mind when creating and working with them.
Simply put, a VPC security group is really just a software firewall. Of course, if things were that simple, then this would be a very short column. As you probably expected, there are some important things that you need to know about VPC security groups.
You can see an example of a security group in Figure 1. As you can see in the figure, each security group contains a collection of inbound rules and outbound rules.
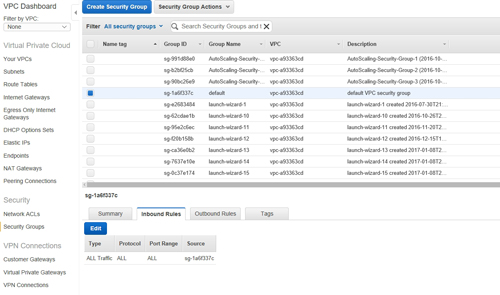 [Click on image for larger view.] Figure 1: VPC security groups are made up of inbound rules and outbound rules.
[Click on image for larger view.] Figure 1: VPC security groups are made up of inbound rules and outbound rules.
The first thing that you need to know about these rules is that although they exist within the VPC, the rules actually apply to individual virtual network adapters. Think of it as applying firewall settings to individual instances (or rather, virtual NICs within an instance).
Another thing that you need to know about VPC security groups is that you can apply multiple security groups to a single network adapter. Doing so results in the rules from the various security groups being combined and collectively applied to the adapter.
Security group rules are designed to grant permission for a particular type of traffic. There is no such thing as a denial rule, because traffic is denied unless there is a rule allowing it. The exception to this is that response traffic is allowed. If, for example, an instance sends a request, then the response to that request will be allowed to enter the instance, even if the security rules would have otherwise blocked that type of communications.
One more thing to keep in mind is that the instances within a VPC are not allowed to communicate with one another unless you explicitly allow them to do so. The default security group does allow communications between instances, but if you choose not to use the default security group, then you will have to create rules enabling any desired communications between instances.
You are, of course, free to use the default security group, but most administrators choose to create some custom VPC security groups to either replace or augment the default group. Before you create any security groups, however, it is important to understand some applicable limits.
Security groups are applied at an instance's network interface. By default, AWS will let you apply up to five security groups to a virtual network interface, but it is possible to use even more in extreme situations (the upper limit is 16). Doing so requires you to contact AWS support.
Another limit that you will need to be aware of is that of the number of rules you can have per security group. Each security group can have up to 50 inbound IPv4 rules, 50 inbound IPv6 rules, 50 outbound IPv4 rules and 50 outbound IPv6 rules. Keep in mind that although there are ways of getting around the default limits, you cannot do so without contacting AWS support. If, for example, you choose not to create any IPv6 rules, that alone does not give you the ability to create additional IPv4 rules.
As previously explained, AWS sets some default limits on the number of security groups that you can assign to a network interface, and the number of rules that can exist within a security group. I also mentioned that it is possible to bend the rules by contacting AWS support and asking them to raise your limits. However, there is one limit that you will not be able to get around: The total number of rules that apply to a network interface cannot exceed 250 (AWS support cannot change this limit).
Hence, increasing the number of security groups that can be applied to a virtual network interface has the potential to reduce the number of rules that you can create within a security group. If you add together the number of rules that exist within each of the security groups that apply to a network interface, that number cannot exceed 250.
There is one last limit that you need to be aware of. By default, AWS sets a limit of 500 security groups per VPC. You can get around this limit by contacting AWS support.
Related:
About the Author
Brien Posey is a 22-time Microsoft MVP with decades of IT experience. As a freelance writer, Posey has written thousands of articles and contributed to several dozen books on a wide variety of IT topics. Prior to going freelance, Posey was a CIO for a national chain of hospitals and health care facilities. He has also served as a network administrator for some of the country's largest insurance companies and for the Department of Defense at Fort Knox. In addition to his continued work in IT, Posey has spent the last several years actively training as a commercial scientist-astronaut candidate in preparation to fly on a mission to study polar mesospheric clouds from space. You can follow his spaceflight training on his Web site.